Date: 22-10-23
Fhenix Rising: The First Fully Homomorphic Encryption-Powered L2 to Bring End-to-End Encryption for Web3
Fhenix leverages cutting-edge Fully Homomorphic Encryption (FHE) technology to introduce for the first time native encryption capabilities into EVM smart contracts, enabling computation over encrypted data. This enhances data security and privacy to unparalleled levels, unlocking a multitude of innovative Web3 applications.
Introduction
It’s become increasingly clear that Web3 is the future, but blockchain’s innate transparency presents challenges that inhibit the industry’s growth trajectory. This is because a growing number of Web3 use cases revolve around sensitive data, rendering the full openness of public blockchains problematic.
This is for two main reasons:
- Exclusion: Payments, voting, medical records, decentralized identity, and countless other use cases require confidentiality. As the scope of blockchain grows, the absence of robust encryption solutions could either push these applications off-chain or force them to compromise on data confidentiality.
- Security: On-chain data transparency makes it much simpler for malicious parties to identify and target users. This has led to billions lost through phishing attacks and other exploitative tactics like MEV extraction.
While in Web2 space data encryption is a well-established and required standard, it seems that the ‘lack-of-encryption’ for commercially sensitive and personal data in Web3 is still a growing and evolving threat. To scale the industry forward, privacy must be an integral part of blockchain, meaning that data encryption and computation capabilities should be key features of all blockchains.
To address this challenge we need to bring developers the infrastructure and tools that allow easy integration of robust data encryption capabilities in the applications that are essential for this space to grow.
Fhenix is rising to this challenge.
Fhenix is building the first confidential smart contract platform using fully homomorphic encryption (FHE). FHE is a novel cryptographic scheme that enables direct computation over encrypted data without ever revealing the underlying data. Fhenix’s goal is to advance application development in the blockchain ecosystem by bringing data encryption and encrypted data computation to smart contracts, transactions, and on-chain assets for the first time.
By leveraging the power of FHE, Fhenix redefines how sensitive data is being managed in the blockchain ecosystem, envisioning a future where privacy and decentralization are not at odds, but rather, complementary aspects of a secure digital economy.
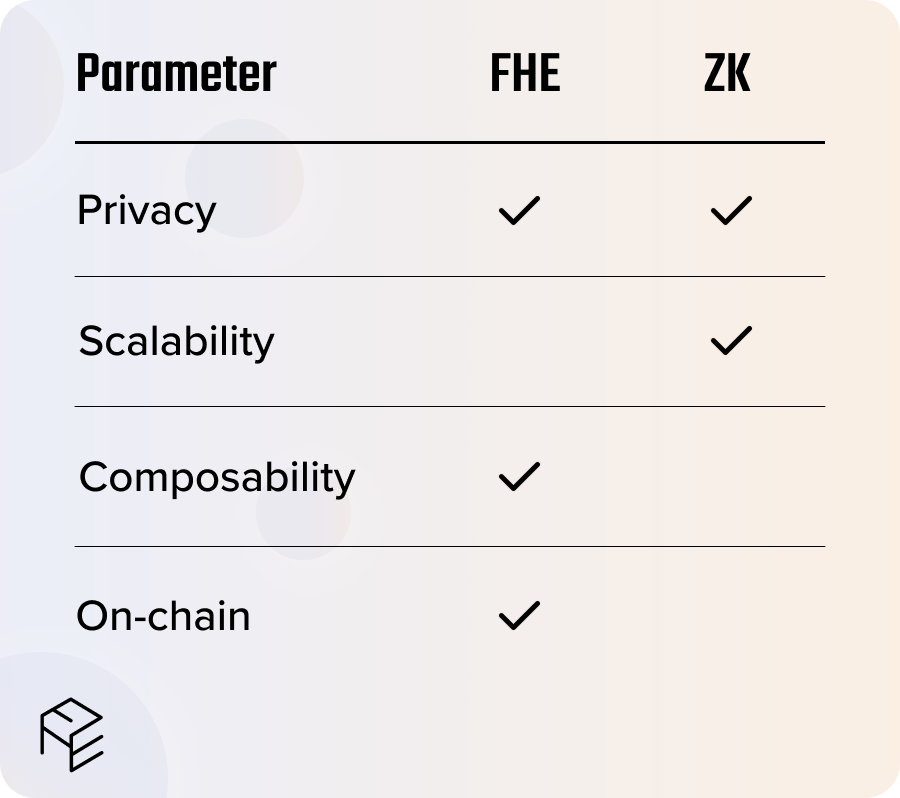
Fully Homomorphic Encryption
FHE is considered the holy grail of cryptography, as it enables direct computation over encrypted data while never revealing the data to the server, or in the context of blockchains — to validators or sequencers. This is all groundbreaking, with recent breakthroughs paving the way for Homomorphic Encryption data processing to arrive at last on the blockchain.
This means that Fhenix now enables a wide array of versatile use cases such as:
-
- Trustless Gaming: Every game that requires players to hide their information from other players, like on-chain casino gaming, where you need to hide information between opponents or the dealer, while still allowing computation on the data.
- Private Voting: Both on-chain and off-chain voting mechanisms can operate with fully encrypted variables, ensuring confidentiality without sacrificing trustworthiness.
- Privacy-Preserving AI: The ability to compute encrypted data opens the door for on-chain artificial intelligence applications, thereby expanding the range of possible use cases exponentially.
- Confidential Token Transfers: P2P payments, commercial transactions, and other sensitive transfers can be made private, yet auditable.
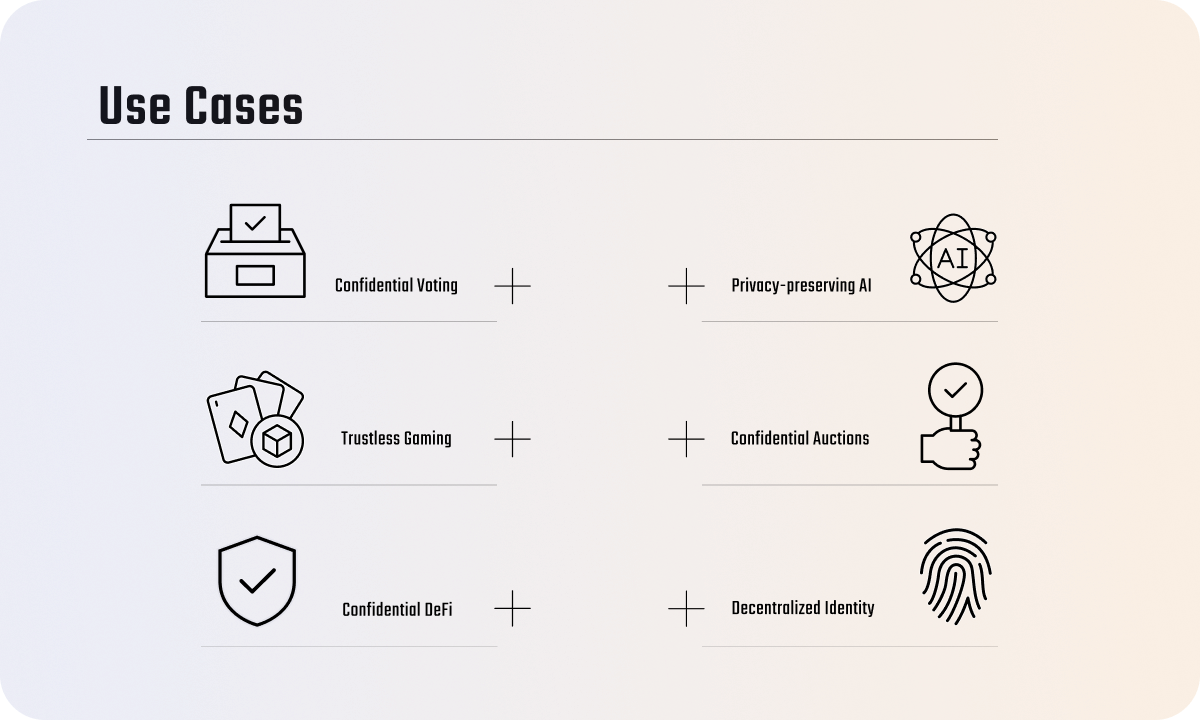
These are all multi-billion dollar industries growing at a rapid pace, but applicability also extends to areas such as blind auctions, MEV protection, account abstraction, and confidential DAOs. We are also merely at the beginning of what’s truly possible, with many use cases undiscovered.
This is all possible due to fhEVM, which we’ll cover next.
The Gold Standard: fhEVM
fhEVM is a set of extensions for the Ethereum Virtual Machine (EVM) that allows Solidity developers to seamlessly create encrypted smart contracts without any cryptographic expertise. Solidity is the most popular Web3 language to date and comes with an extensive suite of developer tools and libraries, making fhEVM extremely easy to begin working with.
This is important, as blockchains that rely upon entirely novel programming languages have significant costs associated with attracting and training developers to begin using their unique language. In contrast, fhEVM taps into the expansive EVM community and enables developers to easily begin deploying new, innovative projects.
Fhenix also has a modular, extension-like design which means that its ability to compute encrypted data can be integrated across all blockchain layers, enabling the easy development of confidential smart contracts on public blockchains. For example, developers can now build applications around encrypted data, such as decentralized email services or private voting.
This comes in the form of the Fhenix SDK which can now be used by developers to add encryption capabilities to their existing products, seamlessly, without any changes to their existing smart contracts.
Fhenix’s limited access devnet was deployed in July 2023, and provides an approachable FHE playground where the fhEVM is already functional and in use. To apply for early access click here.
The Confidential Compute Constellation: Blockchain’s Encryption-First Future
While public blockchains are pseudonymous in nature, this is insufficient for many blockchain applications and will become increasingly easy to correlate on-chain activity with real-world identities. Also, It is important to understand that confidentiality is not a “one-size-fits-all” issue solved by one technology alone. Like in blockchains, there are multiple tradeoffs between confidentiality technologies, such as security, scalability, decentralization, complexity and cost.
This insight led to the formation of the Confidential Compute Constellation: a collective of interconnected confidential solutions serving as an encryption hub for Web 3.0.
The Confidential Computing Constellation starts by combining Secret Network’s battle-tested platform, experience and community with the novel Fully Homomorphic Encryption technology that Fhenix introduced into a full-fledged smart contract platform.
The goal of the Constellation is to combine a wide range of confidential-computing technologies and solutions to create a single hub for privacy and confidentiality on Web3, offering confidential computing applications on member networks and providing privacy as a service to the EVM ecosystem and beyond.
Encryption Allstars: The Team Behind Fhenix
Fhenix was founded by Guy Zyskind, the Founder of Secret and is led by Guy Itzhaki, a former Director at the Homomorphic Encryption & Blockchain Group at Intel.
Forged by a partnership with Zama, a market leader in fully homomorphic encryption technologies, Fhenix team is composed of the world-leading experts in private computation solutions.
“Fhenix addresses a huge problem in the Ethereum ecosystem: a lack of encryption for commercially sensitive data,” said Guy Zyskind, Fhenix and Secret Founder. “Fhenix gives users the confidence to put sensitive data on public blockchains while also giving developers the tools to compute and transform that data for the first time.”
Fhenix recently raised a $7.5M Seed Round co-led by Multicoin Capital and Collider Ventures, with collaboration from Node Capital, Bankless, HackVC, TaneLabs, Hashkey and Metaplanet. The funds will be used to bring the Fhenix Network into public testnet early next year and to support ecosystem application development.
Blockchain’s Renaissance: Upcoming Public Testnet
FHENIX’s public testnet titled Renaissance will be open for participation in Q1 of 2024, inviting developers to familiarize themselves with the fhEVM environment and build novel applications. This is particularly exciting for developers keen on being first-movers in an emerging field of blockchain, and more details will be shared in the coming weeks.
We invite those interested to apply for early testnet access here.
Join our social media channels to get all the updates!
Fhenix: Programable. Scalable. Encrypted.