Date: 22-10-23
The Holy Grail of Encryption: The Rise of FHE Technology
Fully Homomorphic Encryption, once considered impossible by leading cryptographic experts, is finally here. It is encryption’s unicorn technology, allowing for the arbitrary computation of encrypted data and in turn ushering in the new era of confidential computing.
For years, cryptography researchers have battled with the fact that while data can be encrypted in transit, actual data processing requires that data be first unencrypted. These additional steps present data vulnerabilities and have contributed to major data breaches impacting hundreds of millions.
Groundbreaking research from leading academic cryptographers, alongside advances in computing power, have at long last brought us Fully Homomorphic Encryption: the ability to conduct secure operations on encrypted data.
In this post, we’ll cover:
- What is Fully Homomorphic Encryption?
- How does it work?
- And, what can it do?
Let’s dive in.
What is FHE?
In 1978, researchers first examined the issues surrounding modifying computer hardware in order to perform secure operations on encrypted data. For the following 30 years little progress was made, primarily due to insufficient computing power required for such complex computations.
In 2009, progress resumed when a possible FHE scheme was proposed by Craig Gentry. This coincided with significant increases in computing power that fueled early progress in artificial intelligence. Further progress has since been made, including a groundbreaking research paper in 2013 that sidestepped FHE’s computationally expensive relinearization step, have helped lead us to the present day.
At long last, the “once mythical” technology known as Fully Homomorphic Encryption has arrived, allowing us to conduct confidential computing. At its core, confidential computing introduces a totally new paradigm of securing data, and performing secure computations.
So what does Fully Homomorphic Encryption actually mean? Let’s consider each term separately:
- Fully: In the context of FHE, fully means that arbitrary operations such as addition and multiplication are supported.
- Homomorphic: The ability to allow computations on encrypted data without first decrypting it.
- Encryption: The process of converting information into code that prevents unauthorized access.
Taken together, FHE refers to the ability to perform binary operations on encrypted data without decrypting the data — ever. Kind of like magic.
Binary operations refer to mathematical operations that take two inputs and produce a single output — such as addition, multiplication, subtraction, and division. Blockchains, at their core, primarily deal with integer operations, meaning that this is tremendously valuable for the industry as a whole.
FHE’s Significance to Blockchain
The status quo requires data to first be decrypted in order to run computations on it. It must then be encrypted again, and later decrypted, with each step presenting new opportunities for the data to be exploited.
This has contributed to major data exploits in nearly every industry, impacting hundreds of millions and the biggest firms including Equifax, Marriot International, EasyJet, and countless more. Each exploit of sensitive data costs billions to rectify, and exposes the personal data of millions. FHE’s ability to compute encrypted data has far reaching ramifications for nearly every industry and will become the new standard for data security.
How can this be implemented?
While future content will cover FHE at a technical level, here we will provide a simple overview in regards to how FHE would integrate in blockchain. Keep in mind that FHE has far reaching implications beyond just the blockchain industry — but this space is our focus.
As mentioned, blockchains primarily deal with integer operations, such as managing smart contract “states”, updating block indices, or processing cryptocurrency transactions. This means that applying FHE onto encrypted blockchain data is extremely powerful.
That being said, FHE is niche and very complex, so the barrier to entry is high. That’s why we’ve partnered with Zama, which built the fhEVM.
fhEVM is a set of extensions for the Ethereum Virtual Machine (EVM) that allows any Solidity developers to integrate FHE into their workflow. This enables the creation of encrypted smart contracts without any FHE expertise and means that developers can benefit from Solidity’s extensive suite of developer tooling.
fhEVM is used for writing the application itself, but we also have fhenix.js which allows developers to create the frontend using Javascript.
FHE vs. ZK
Zero-knowledge (ZK) technology has been widely covered in recent times, often heralded as the future of blockchain privacy.
It’s important to note some distinctions from FHE:
- Encryption computation: ZK cannot compute over encrypted data from multiple users (which would be the case for private ERC-20 tokens) without sacrificing security. FHE can do so, which makes it more composable throughout blockchain. ZK technology often requires custom integrations for new networks and assets.
- Scalability: ZK is considered more scaleable than FHE, at least at the present moment. Technological developments will scale FHE over the coming years.
- Complex calculations: FHE can handle complex calculations on encrypted data, suitable for needs such as machine learning, secure MPC, and fully private computations. In contrast, ZK Proofs are typically users for simpler tasks such as proving a value without revealing it.
- Universal Applicability: while ZK Proofs are great for specific use-cases like identity verification, authentification, and scalability, FHE can be applied to a broader range of applications. This includes confidential data processing, secure cloud computing, and privacy-preserving AI applications.
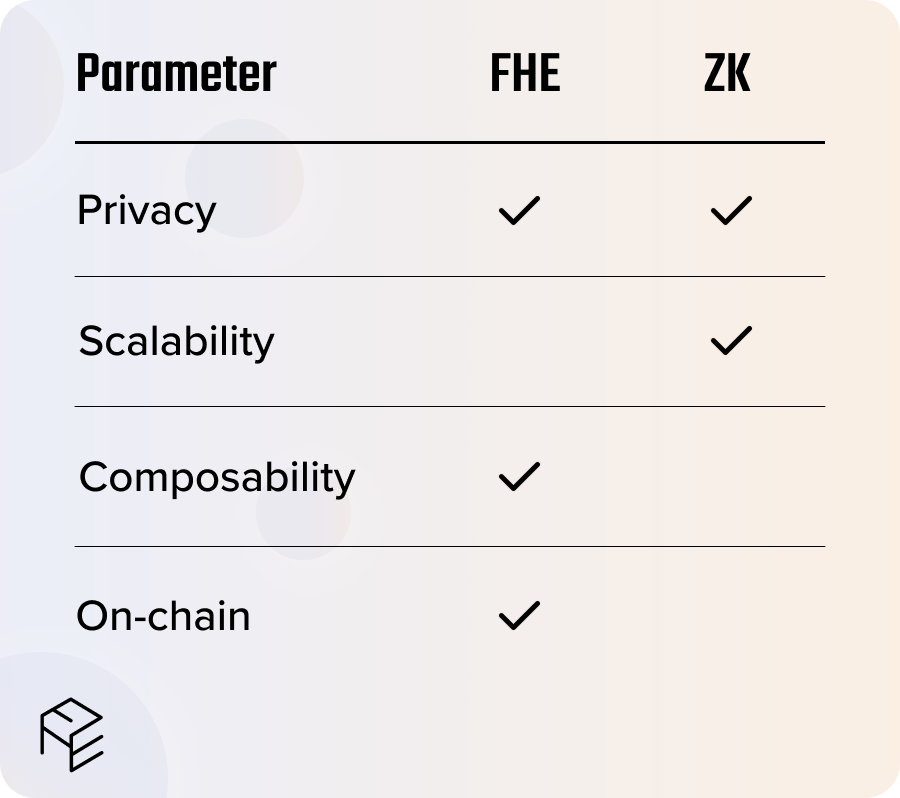
We believe that both have their place in blockchain. However, while ZK technology is more mature than FHE at the present moment, we believe that FHE will ultimately emerge as the most suitable privacy-preserving solution.
For more information, we covered the fhEVM in greater depth in our last blog post.
Conclusion
FHE represents a breakthrough for confidential computing
The above article aimed to provide the reader with a fundamental understanding of FHE, including:
- how it came to be,
- how it works, and
- its implications for blockchain as a whole.
No longer must data be unencrypted in order to have computations run — it can now remain encrypted the entire journey, vastly reducing the number of attack vectors. This also means that many institutional blockchain use-cases are now feasible, as data privacy is a key consideration for them.
Future content of ours will cover FHE at a more granular level. In the meantime, if you are interested in getting started, you can learn more about the process here.
Join our social media channels to get all the updates!
FHENIX: Programmable. Scalable. Encrypted.