
Date: 16-11-23
Introducing FHE-Rollups: Scaling Confidential Smart Contracts on Ethereum and Beyond
This article will provide a simplified overview of our technical whitepaper’s first iteration. Given that our work concerns cutting-edge technical research, we will be continuously updating it to incorporate our latest breakthroughs and technological advancements. This makes it a rolling whitepaper of sorts.
The technical white-paper can be viewed here.
One of the central challenges for Ethereum and other EVM (Ethereum Virtual Machine) networks is their inherent public transparency, which limits widespread adoption by hindering use cases that require privacy. Our whitepaper—and this accompanying article—introduces Fully Homomorphic Encryption (FHE) Rollups, an innovative approach to infusing EVM-based networks with confidentiality.
The significance of FHE Rollups cannot be overstated, especially because they unlock the potential for sensitive and private data to be processed securely on Ethereum and other EVM networks. Such advancement means that institutions can conduct private on-chain transactions, and it opens the door for additional applications like confidential trustless gaming, private voting, and more.
What sets FHE Rollups apart is that they allow developers to build confidential smart contracts using an optimistic rollup structure. Developers wishing to use our FHE Rollup will benefit from both the scalability of a rollup and the ability to introduce encryption into their applications, using familiar EVM programming languages that are part of our FHE libraries.
While our whitepaper is rather technical, this article aims to be a companion that provides a simplified overview, covering topics such as:
-
A quick review of Fully Homomorphic Encryption
-
The need for confidential smart contracts
-
L2 rollups
-
Our design choice & implementation procedures
We demonstrate through a proof-of-concept (PoC) implementation, that an optimistic FHE rollup can be built on top of Ethereum without any changes to the base layer.
FHE Encryption – A Quick Primer
In a recent blog post, we covered Fully Homomorphic Encryption (FHE), a cutting-edge technology that allows computation over encrypted data. Research into FHE began in the late 1970s, but only recently has computing power and technology advanced enough to bring it to fruition.
The computation of encrypted data has far-reaching implications across many industries but is particularly important for blockchains where data is publicly visible. By encrypting data on the blockchain and being able to compute upon it, use cases revolving around sensitive data become possible. This could include trustless gaming, private voting, and privacy-preserving AI, but we expect the full range of possibilities to be much greater. It also includes institutional use cases, such as payments, which would otherwise not be possible without sacrificing privacy.
Implementing FHE on the blockchain, especially on the Ethereum Virtual Machine (EVM), brings privacy to the blockchain and is a critical advancement for the space.
The Move Towards Rollups
Ethereum and EVM-compatible networks are leading the blockchain race but suffer from scalability limitations. A Layer 2 (L2) architecture has been proposed by leaders in the space (such as Vitalik Buterin) as Ethereum’s primary proposed scaling solution.
While Ethereum typically works by handling both execution and consensus itself, an L2 handles execution off of Ethereum. Transactions are then “rolled up” into one big update that is periodically sent to Ethereum for settlement. This is significantly more efficient given that smart contract execution is the heavy-duty part of block validation, but security is maintained as these executions are then sent to Ethereum for validator consensus.
There are two primary architectures for L2s:
-
Optimistic Rollups: Transactions are assumed valid unless otherwise challenged. They post all transaction data to Ethereum, allowing anyone to verify for themselves that the off-chain execution was done correctly. If any verifier detects malicious behavior, they can submit a fraud-proof on-chain which instigates a dispute process.
-
Zero-Knowledge (ZK) Rollups: Rather than post transaction data on-chain, they submit cryptographic proofs. These proofs are constructed using advanced cryptographic techniques known as ZK Proofs. They can be efficiently verified on-chain directly, without posting the full transaction data or having a dispute period.
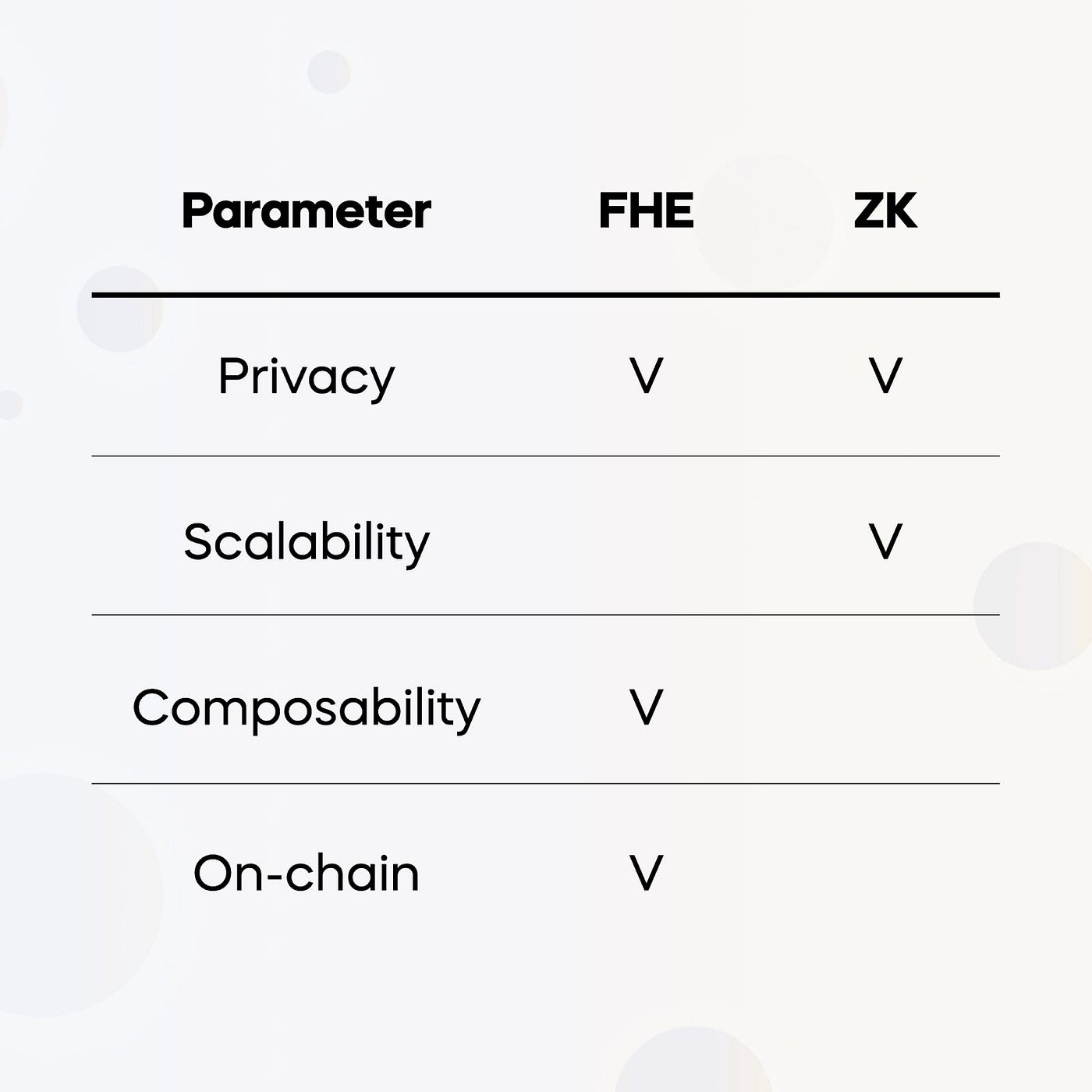
Optimistic rollups require a dispute period but are much easier to implement than ZK Rollups. The reason for this is that ZK Rollups require significant computational power (and time) to create ZK Proofs, and are also much more complex to build. This also provides room for error in the code, which should be minimized.
If we were to implement our platform as a ZK Rollup, we would be combining two heavy-duty cryptographic techniques together. While research in this space may advance over the coming years, at the present moment the implementation of FHE through an optimistic approach is much better. A ZK approach would be orders of magnitude less efficient.
Therefore, we have chosen to implement the FHE Rollup as an optimistic rollup.
How does this work?
At a high level, we ensure data integrity by running a variation of Arbitrum Nitro’s fraud prover, which can do fraud proofs over the WebAssembly Virtual Machine (WASM). This has allowed us to compile FHE logic to WebAssembly and run it in a secure way on WASM code, rather than on the native Ethereum Virtual Machine (EVM) itself. Without using Arbitrum Nitro’s fraud prover, there would be challenges given that Ethereum does not natively support FHE operations.
Existing Solutions
The FHE Rollup is not the first proposed confidential smart contract platform.
Some existing solutions include:
-
Trusted Execution Environments (TEEs): transactions are decrypted and computed upon within a secure environment. TEEs are already in production and considered quite efficient, but they require reliance upon the environment’s security and are susceptible to vulnerabilities such as side-channel attacks.
-
Secure MPC: similar in nature to the FHE Rollup but use linear secret-sharing and garbled circuits rather than FHE technology. A drawback to this approach is that it is challenging to manage as data loads increase. it is also not suitable to a rollup architecture.
-
Zero-Knowledge (ZK): ZK techniques are more suited for verifying computations, instead than actually running confidential smart contracts.
Our FHE Rollup PoC is instead the first solution that operates fully and natively as an L2. This means that we have built a platform whereby FHE technology is built directly into the network, rather than being an external technology that comes with associated vulnerabilities and/or limitations.
Below we’ll provide an overview of our design that enables this.
Design Overview
Our platform aims to be modular which means it separates different components of the blockchain. In particular, it separates the Sequencer, Validator, and Data Availability (DA) layers. Ethereum handles the data settlement and DA component, while Fhenix handles the Sequencer (execution) and Validator (transaction validation).
This separation of components allows FHE Rollups to execute more efficiently while still having the necessary access to Ethereum’s DA.
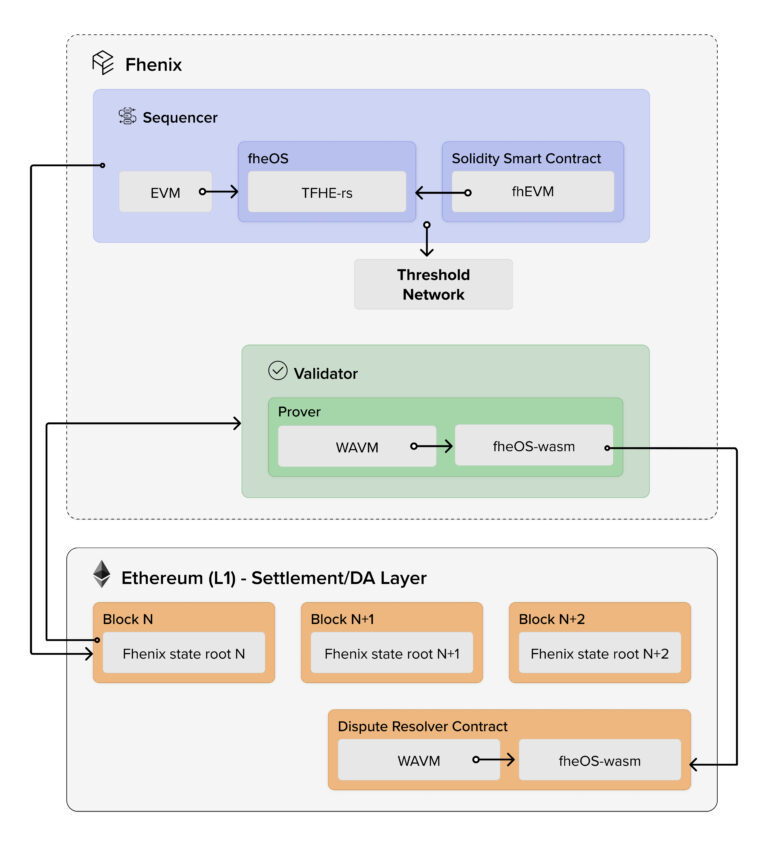
The core FHE logic sits in our fheOS library. It is a programming library that contains everything that a developer needs to begin implementing FHE logic into their smart contracts. There are other components to fheOS, such as the TFHE-rs, which is a full FHE library built by our partner Zama. These technical specifications are beyond the scope of this article but we will cover them in future pieces.
A key technology used is our Threshold Services Network (TSN), useful for tasks such as decrypting data when necessary. An example of decryption being necessary could include announcing the outcome of a vote, which requires tallying votes. The TSN would decrypt the data and then return it. More information on the TSN can be found in the full whitepaper.
Bringing Things Together
As a summary, the first iteration of our whitepaper has proposed the construct of an FHE Rollup: a novel solution that adds confidentiality to Ethereum and other EVM chains.
Developers can use this to build Layer 2s with built-in encryption capabilities, putting them at an advantage over rival networks. This is also simple to implement, as developers can use familiar EVM programming languages, rather than being required to learn an entirely new language. We essentially make it easy for anyone to benefit from our cutting-edge FHE research.
We chose an optimistic oracle architecture as it best suits our needs, and avoids the cost of replicating expensive FHE computations across all Ethereum nodes. At the present moment, implementing FHE with a ZK architecture is not a realistic approach, but we are also closely monitoring and progressing in this realm as well.
This will help usher in a new era of confidential computing that will unlock new Web3 use cases and help to drive blockchain adoption.
The full white-paper can be viewed here.
We also recommend visiting our website at fhenix.io to learn more.

Unlocking Encrypted Computation on Arbitrum: CoFHE Is Live on Testnet
28 Apr 2025

Fhenix and zkPass: Bringing Secure and Confidential Identity and Reputation Verification Onchain
18 Jul 2024

Introducing CoFHE: FHE-Based Encryption Everywhere With a Single Line of Code
7 Apr 2025